What is a crypto wallet for beginners?
A wallet is an electronic wallet, capable of holding within it the private keys of our cryptocurrencies.
We can imagine it just like the wallet we put in our pocket or purse every day. Instead of storing cash and payment cards, this tool will house our digital assets-Bitcoin, Ethereum, other coins and tokens, NFTs.
This comparison works to identify functionality and nature of a wallet; however, to be accurate, it is not quite correct. Rather, we should say that a wallet is more like a keychain.
Confusion? Continue reading to eliminate it!
Index
Difference between private and public key
When a wallet is created, two keys are generated: a private and a public key. In short, the public key is the address I have to give to a third party when I want them to send me funds, similar to a bank IBAN. In contrast, the private key is for me to spend the funds I hold.
This is an example of the public key/address of a Bitcoin wallet: bc1qqlvzjms********************teas63rfpfd. This alphanumeric code representing the public key is derived, via a cryptographic function, from the private key.
Instead, here is an example for the Ethereum blockchain: 0x383175***********************************g3Le1
In contrast, the private key cannot be derived anywhere. It is an origin key and it is extremely important that it remain secret for obvious security reasons.
This is why we have mentioned an image of a wallet as a key fob: within it reside our keys, the public key and the private key.
Contrary to what is often thought, this tool does not store our cryptocurrencies: they are and always will be on the blockchain. The wallet has only the function of holding the private keys that we need to access the digital currencies.
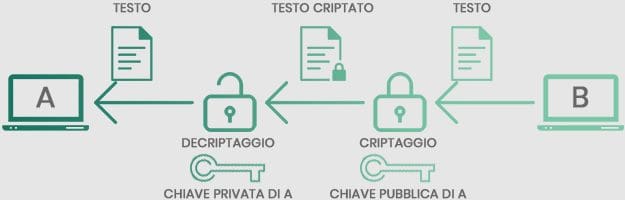
As you can see from the image below, computer B wants to send information to computer A.
Through the first step, the encryption step, B uses A’s public key to encrypt the information, making the text secure and not visible to anyone.
After that, A will use his own private key to decrypt the information and read the message sent by B.
While there is a lot of complexity behind the scenes, the concept is quite simple, isn’t it?
What wallet to use?
Let us now discuss how a wallet is generated, the differences there are between different types of digital wallets, and which one to use.
There are two main categories of this tool. They define who holds the private keys and, consequently, who is the true owner of the coins associated with that address: custodial wallet and noncustodial wallet.
For better understanding, let us address them in separate paragraphs.
Custodial wallets
Picking up on the analogy comparing crypto wallets to the means of holding money in the real world, we can say that a wallet opened within an exchange can be viewed like a bank account. There is one important difference, however: the absence of insurance on our funds.
As the name suggests, the custodial wallet delegates responsibility and possession of the private keys within it to a custodian. This means that although we continue to be the users of the wallet, we will no longer be the actual owners of the coins it contains.
The most emblematic case of a custodial is that of so-called exchange wallets.
When we deposit currencies within an exchange we lose the real ownership of those coins. Simply put, if the company goes bankrupt or closes down for some other reason, we lose all the capital within it. It has happened before; it is not something impossible.
On the other hand, it should be remembered that it is also and above all in the interest of the exchange itself to guard users’ funds as best as possible, unless we are facing a case of fraud or mismanagement. Always better to be careful, especially in bearish and uncertain periods.
In light of what has just been written, we should protect ourselves and find a way to become the sole holders of cryptocurrencies.
Here is where noncustodial wallets can come to our aid.
Non-custodial wallets
If custodials can be seen as bank accounts, noncustodials are comparable to wallets or safes.
The wallet could be what is called a Hot Wallet. A Hot Wallet is ready for use on any decentralized application because it is always connected to the Internet and, therefore also more exposed to the risk of a possible cyber attack.
In contrast, the safe could be what is called a Cold Wallet, a wallet that is not necessarily connected to the Internet and therefore less susceptible to attack by a hacker.
In either case we will be solely responsible for the coins. It will therefore be necessary to learn as best as possible how they work and how to protect them, so as to avoid making irreversible or difficult to fix mistakes.
Usually hot wallets are free. There are hundreds of types whose differences are minimal; the purpose is always the same: to be able to allow us to interact with our coins.
There are two types of hot wallets: browser extensions and desktop applications.
The former, once downloaded will appear in the browser at the top right of the URL. They are usually chosen for use by decentralized applications, as they are the most immediate wallets. MyEtherWallet and MetaMask are among the best known.
In contrast, desktop applications must be downloaded and installed on our computer. They will use an application of their own to function, just like any other pc program. The procedure is therefore more cumbersome but still quite simple.
Cold wallets also fall into two categories, although there is not as wide a choice: hardware and software wallets. Both are applications that are installed on the computer or cell phone, but the first type also has a physical component that is used to confirm each transaction.
Having a hardware component is critical to being able to prevent almost any hacker threat: even if someone managed to gain access to your computer they would miss the actual object that confirms each transaction. Brilliant, no?
Unlike others, hardware wallets (improperly called crypto sticks or cryptocurrency sticks) come at a cost. The top companies currently producing them are two: Ledger and Trezor.
Ledger produces two models: Nano X and Nano S Plus. Here is a link to the Ledger store, where you can purchase your device.

Paper wallet
The last type of wallet I am going to tell you about is the paper wallet. In fact, creating it means writing a copy of the private key of one of your coins on a piece of paper.
Again, the risks exist and they are not few. We will escape a cyber attack but we could lose our private keys in other ways: lose the paper, lose it, suffer theft, damage it in some way, etc. Without these papers, it would be impossible to recover cryptocurrencies.
The paper wallet falls into the category of noncustodial wallets. However, since it is totally different from the examples seen so far, we have separated it from the others to be clearer about the order and differences.
"The Custodial Wallet entrusted to the Exchange can be compared to a Bank account. The Non Custodial Wallet is more like a wallet or safe, whose responsibility is ours alone."
How to create a non custodial wallet
Creating a non custodial wallet is not complicated and in most cases will not even cost you a Satoshi.
In fact, it will be enough to go to the official sites of the various projects that develop wallets to download the most up-to-date, secure and, above all, suitable version for our needs.
As for hot wallets, the best and most widely used are the aforementioned MetaMask, MyEtherWallet and Trust Wallet.
While as for the cold ones, the most widely used are Ledger and Exodus.
Choosing the right wallet must take into consideration not only security, cost and practicality. In fact, it is crucial to consider which cryptocurrencies we intend to hold and move.
If we wanted to deal in BTC, we should, for example, use a dedicated tool such as Electrum or Ledger. MetaMask and Phantom, just to name two, would be out of the picture instead (they do not support the blockchain).
A wallet does not necessarily support other blockchains. To say, Electrum is dedicated only to this network. In contrast, Exodus works on both BTC and Ethereum, as well as others.
A simple search will suffice to find what works for us in a few minutes. Remember that on this site you will find lots of supporting material: take advantage of it, it’s free!
Seed phrase
Whether we are generating a hot or a cold wallet, there are always 12, 18 or 24 reset words at the base, known as a seed phrase.
The seed phrase is like an additional password that goes on top of the private keys, even if those keys are already encrypted. For example, if we wanted to connect to our wallet from another device, all we would have to do is enter the phrase to restore our wallet and regain possession of our coins. Here is a 12-word example:
surround absent recycle all
nuclear hotel arch code
glimpse stuff middle track
These words will have to be transcribed on a sheet of paper or agenda designated for this purpose. The person who will have the words will own the wallet, so it is imperative to keep them safe. Not recommended to keep them on computer documents as you are exposed to possible attacks; caution is never too much.
It is important to understand that the seed phrase serves only as a recovery item in case the wallet is lost or re-installed on another device.
In fact, to login to a wallet installed on a computer, browser or smartphone we will simply have to enter the password chosen when creating the wallet itself.
Again, we still choose a password that is valid and not obvious. Protecting our wallet with a phrase like hello123 would be a risk, especially if the wallet itself is installed on a portable device and can fall into the hands of others.
Wallet: conclusions
Having reached the end of this article, you have all the facts to figure out which wallet best suits your needs. Thanks to our tutorials you will be able to move forward completely on your own.
Remember that having cryptocurrencies also means acquiring responsibility for your own funds. In fact, unlike fiat currencies, these new digital assets have no guarantees and every action we take is irreversible, whether it is a wrong click or an injustice.
Same with hacker attacks, one of the main reasons why we will not only have to watch out for passwords and seed phrases, but also for the safety of the device.
For an extra step in protecting our keys and passwords, here are a few extra cautions:
- Have a good antivirus;
- Use a VPN. NordVPN is the best around and thanks to our referral you can get it at a super discounted price;
- Create and use a different password for each site;
- Use a dedicated machine for financial transactions. This way the computer will be dedicated only to that specific function. It will then be less likely to run into viruses and malware.
What can we say, good investments and utmost care, see you next time!

